To avoid confusion, information on this website is educational in it’s nature – it is not required to know all of it while you are using the blockchain. It is, however, useful to know how the blockchain works, and why it is impossible to defraud it, or to potentially steal someone else’s coins.
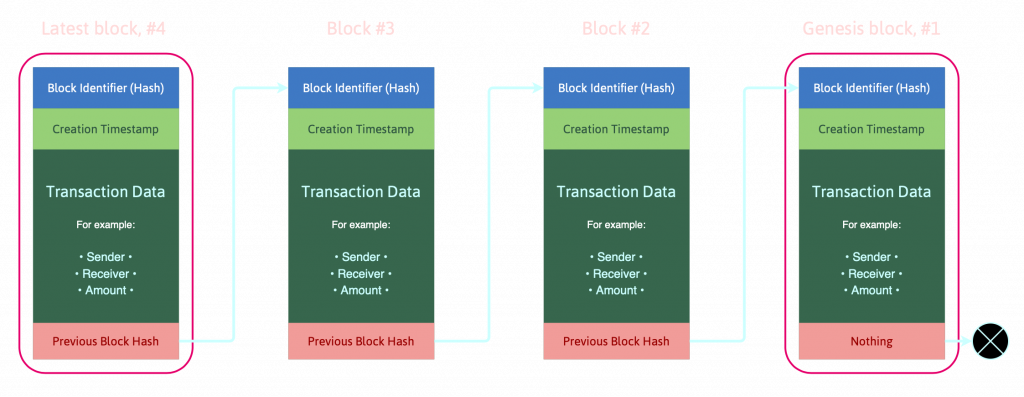
Crypto-currency platforms are typically based on blockchains. Blockchain is a computer structure for storing data – it’s an infinite list of records that are often referred to as “blocks”. We visualize this list of data-blocks as “a chain”, because each block in the list contains information about the previous block in the chain. This is accomplished by assigning a unique cryptographic identifier to each of the blocks. We call this identifier as a “hash”. Alongside it’s own hash and the hash of the previous block identifier, each block can carry additional data, like a timestamp of when the block was created, how much value has been sent or some other transaction data.
Don’t worry, it’s not as scary as it sounds.
In the Bitcoin network, for example, this transaction data is information about origin, destination and amount of Bitcoin transferred from origin to destination. To simplify, we can say: all transactions in a blockchain are linked together using software, and its contents are protected using strong cryptography principles.
Software behind cryptocurrencies
By design, a blockchain is resistant to modification of data. When used in crypto-currency platforms, blockchain is often referred to as “the ledger”. This ledger is fully distributed, there is no single entity governing how the protocol works and what it does. If we use as a distributed ledger, the blockchain is typically managed by a peer-to-peer computer network. Each member of that peer-to-peer network is often called “a node”, and each node connects directly to other nodes without any intermediaries. Once recorded in the ledger, the data in any given block cannot be changed retroactively without also changing all of the blocks that came after it, and in order to achieve that, the majority of the network participants would have to comply (to achieve consensus of the network majority). It’s safe to assume that the majority of all network nodes are not malicious players, thus the network is considered to be safe and fully decentralized using the consensus verification protocol.